In today’s complex financial landscape, middle market and larger companies need a bank that understands their business and their industry. Key’s deep market expertise and relationship-led approach allow us to recognize opportunities and deliver strategic financial solutions that align with our clients’ goals.
Why Clients Choose Key
Over its 200-year history, Key has become one of the nation's largest bank-based financial service companies.

Capital and Lending Access
Flexible financing and
capital markets expertise
to power growth and investment.

Payments and Technology
Streamlined platforms and
real-time guidance to help
mitigate risk and manage liquidity.

Key Wealth Management
Trusted expertise, strategies
and insights to grow,
manage, and preserve wealth.
Our Services
Whether it’s access to capital, industry insights or guidance to drive growth, Key provides resources businesses rely on to compete in a changing economy. See how the strength of a top financial institution and hands-on service of a leading regional bank can help you take your business to the next level.
Empowering businesses that shape the future.
We’re proud to work with commercial clients, businesses and organizations whose innovative ideas and execution have a lasting impact on people’s lives.
Stephanice Washington: Being homeless, not knowing when you got to go, taking your income, spending the whole income up to have a room for a night or two or three. Then having to eat out. Wasn't able to cook and stuff. Having to eat out. You know, that was a lot. I lost everything. I lost everything but the clothes I had on my back.
Robert L. Likes: KeyBank has an unwavering, deep commitment to affordable housing. Our mission and our objectives are to be a national leader in affordable housing, to help the bank always achieve an outstanding CRA rating. To be a major contributor to our community benefits plan and to help our clients and communities thrive.
Erica Haize: We need more affordable housing in this community. So, people are struggling with that a lot. We saw the need of helping people be part of a great community.
Kevin Loos: NRP made an initiative into housing and health care, and so we've created a few projects across the nation, partnering with hospitals to provide housing and health care. You’re next to the healthcare community, next to primary care doctors, next to emergency room help, and really it becomes a more of a wraparound type of service, being right next to the campus.
Robert L. Likes: It's adjacent to a hospital to help with healthy initiatives. It also has community space within the Affordable Housing project that provides job counseling, financial literacy training, digital training, all for the betterment of the tenants and the surrounding community, to help really uplift lives.
Stephanice Washington: The day I got the phone call that I could come in and pick up my keys, was the best thing that ever happened for me.
Erica Haize: This was like a steppingstone for them. Some of them, like I said, were homeless. They start living here, their lives change. Their family can see that their life is changing. And to come in a building like this, and having something so nice and brand new for the first time, it's life changing.
Stephanice Washington: Before I came to Via Sana, my whole check went on my light, my gas, my rent. Since I've been at Via Sana, I'm able to save up, so I'm able to go to Walmart and buy me a month's worth of food from my income now.
Erica Haize: I hope we can partner more so we can keep making a change in the community.
Robert Likes: Affordable Housing changes lives. There are so many positive, healthy outcomes and economic upward mobility, when you have a permanent residence that is safe, decent, clean, affordable, that is your home.
Stephanice Washington: My new apartment is my serenity, my peace, and my home.
Recent Deals
Key brings extensive experience in closing deals across industries to help clients strengthen their market position and achieve greater success.

$750 Million
Senior Notes
Active Joint Bookrunner
Summary
On February 26, 2026, KeyBanc Capital Markets served as Active Joint Bookrunner on a $750 million Senior Notes offering for Matador Resources Company. Proceeds will be used to repay existing indebtedness, and for general corporate purposes.

affiliated with

Sell-Side Advisor
Summary
Cain Brothers, a division of KeyBanc Capital Markets, served as exclusive sell-side advisor to Central Maine Healthcare in its affiliation Prime Healthcare Foundation.
Cain Brothers was engaged to assist in the negotiations and affiliation process due to its domain expertise and understanding of the New England healthcare market. The affiliation will help achieve Central Maine and Prime’s joint long-term commitment to deliver the highest quality, most advanced health care to communities across central, western, and mid-coast Maine. The agreement includes continued local governance and management, ongoing community commitment and significant capital investment in the region.
Central Maine Healthcare is an integrated delivery system serving 400,000 people in central, western and mid-coast Maine. With over 600 physicians and advanced practice professionals in more than 40 locations, CMH includes Central Maine Medical Center, a Levell III Trauma Center in Lewiston, as well as critical access facilities, Bridgton and Rumford hospitals, and two long-term care communities.
Prime Healthcare is a health system operating 44 hospitals and more than 300 outpatient locations in 14 states, providing over 2.6 million patient visits annually. It is one of the nation’s leading health systems with nearly 45,000 employees and physicians. Fourteen of the Prime Healthcare hospitals are members of the Prime Healthcare Foundation, a 501(c)(3) not-for-profit public charity.

merged with

Lead Financial Advisor
Fairness Opinion Provider
Summary
On February 13, 2026, Olympic Steel, Inc. (Olympic Steel or the Company) and Ryerson Holding Corporation (Ryerson) announced that they have completed their all-stock merger. KeyBanc Capital Markets (KBCM) served as lead Financial Advisor and provided a Fairness Opinion on the transaction.
KBCM was selected to serve as Olympic Steel's lLead Financial Advisor and Fairness Opinion Provider based on the group's deep industry expertise in metals distribution and processing, extensive transaction expertise in complex mergers and acquisitions and a decades-long partnership with the Company.
Founded in 1954, Olympic Steel is a leading U.S. metals service center focused on the direct sale and value-added processing of carbon and coated sheet, plate and coil steel products; stainless steel sheet, plate, bar, and coil; aluminum sheet, plate, and coil; pipe, tube, bar, valves, and fittings; tin plate and metal-intensive end-use products, including stainless steel bollards; commercial, residential, and industrial venting and air filtration systems; Wright® brand self-dumping hoppers; and metal canopy components. Headquartered in Cleveland, Ohio, Olympic Steel operates from 53 facilities.
Founded in 1842, Ryerson Holding Corporation (NYSE: RYI) is a leading value-added processor and distributor of industrial metals. The company offers a broad portfolio of carbon and stainless steel, aluminum, and alloy products, along with extensive metal processing capabilities, including cutting, forming, machining, and fabrication. Ryerson has ~4,300 employees and ~110 locations across North America, Mexico, and China, serving a diverse customer base in industries such as heavy equipment, industrial machinery, and energy.

$219 Million
Senior Secured Credit Facilities
Left Lead Arranger
Joint Bookrunner
Administrative Agent
Summary
On February 12, 2026, KeyBanc Capital Markets, Inc. (KBCM) successfully closed the syndication of $219 million Senior Secured Credit Facilities (the Credit Facilities) for the Soboba Band of Luiseño Indians (the Tribe). The Credit Facilities consist of a $129 million Revolving Credit Facility and $90 million Tax-Exempt Term Loan. Proceeds from the Credit Facilities will be used to refinance existing indebtedness, fund the development and construction of a cogeneration plant (the Project) at the Soboba Casino Resort, and pay transaction-related fees and expenses.
KBCM was selected to arrange and lead the financing due to its long-standing relationship with the Tribe, cultivated through years of partnership and dialogue, along with unmatched experience and expertise in the Native American Financial Services industry, and successful track record of syndicating transactions in the gaming space.
The Project
The Tribe plans to develop and construct a combined heat and power plant to cogenerate electricity and hot water at Soboba Casino Resort. The Project will modernize the property's energy infrastructure through the integration of a microgrid controller, electrical infrastructure upgrades and electric vehicle charging infrastructure. Collectively, these improvements will enable Soboba Casino Resort to generate 100% of its electricity demand on-site and significantly enhance the property's long-term operational resilience.
Soboba Band of Luiseño Indians Overview
The Tribe is a sovereign nation with over 1,600 enrolled members. Since time immemorial, the descendants of the Soboba people are those who have lived on and occupied the land that is presently known as the cities of San Jacinto, Hemet, Valle Vista and Winchester, California. Today, the ~8,000-acre Soboba Indian Reservation lies in the lower reaches of the San Jacinto Mountains, across the San Jacinto River from the city of San Jacinto. The Tribe owns and operates Soboba Casino Resort, an award-winning property that features over 100,000 sq. ft. of gaming space, including 2,000+ slot machines and 30+ table games, and is further complemented by a 200-room hotel, spa, PGA-rated golf course, and more.

$1 Billion
Senior Notes due 2031
$750 Million
Senior Notes due 2033
$1.3 Billion
Senior Notes due 2036
$750 Million
Senior Notes due 2046
Co-Manager
Summary
KeyBanc Capital Markets and Cain Brothers, a division of KeyBanc Capital Markets, acted as Co-Manager in the $3.8 billion offering of Senior Notes for Thermo Fisher Scientific Inc. (NYSE: TMO).
Cain Brothers and KeyBanc Capital Markets served as Co-Manager due to its industry expertise and long-standing relationship with the Company. Proceeds will be used to fund the cash consideration related to the acquisition of Clario Holdings as well as general corporate purposes.
Thermo Fisher manufactures scientific instruments, consumables, and chemicals. The Company offers analytical instruments, laboratory equipment, software, and supplies to pharmaceutical and biotech companies, hospitals and clinical diagnostic labs, universities, research institutions, and government agencies.

acquired

Buy-Side Advisor
Summary
Cain Brothers, a division of KeyBanc Capital Markets, served as buy-side advisor to MyTown Health Partners in its acquisition of MDB Health Services.
Cain Brothers has a long-standing relationship with management and the sponsor, Webster Equity Partners, as well as expertise and unique insight into the target, given a successful track record of advising primary and post-acute care groups. Cain Brothers was engaged to provide strategic guidance as well as transaction and diligence support. The acquisition expands MyTown’s presence across medically underserved communities and strengthens its commitment to delivering coordinated, high-quality clinical services.
MyTown is a physician-led management organization that works with practices in rural communities to improve access and enhance clinical outcomes. With over 50 clinics across eight states, MyTown’s growing network supports clinicians in the delivery of high-quality, outcome-driven primary care, urgent care, behavioral health, and women’s health services in medically underserved markets.
MDB Health Services is a multi-disciplinary provider serving post-acute care facilities in Mississippi, Louisiana, and Arkansas. Founded in 2013, MDB has grown from its origins in behavioral health services to include primary care, behavioral health, wound care, and foot care. MDB’s clinicians deliver coordinated clinical care that is tailored to the needs of residents in long-term care settings.
Webster Equity Partners is a healthcare-focused private equity firm focusing on high impact growth strategies to deliver optimal outcomes for its investors, portfolio companies and the communities that they serve. Its mission is to deliver superior returns to partners through investment and development of patient-centric healthcare organizations.

$5 Billion
Senior Secured Credit Facility
Joint Lead Arranger
Co-Documentation Agent
Summary
On January 30, 2026, KeyBanc Capital Markets served as Joint Lead Arranger and Co-Documentation Agent on a $5 billion Senior Secured Revolving Credit Facility for SM Energy Company. Proceeds will be used for general corporate purposes.

acquired by

Sell-Side Advisor
Summary
Cain Brothers, a division of KeyBanc Capital Markets, served as exclusive financial advisor to National Radiology Solutions in its sale to Premier Radiology, a portfolio company of Grovecourt Capital Partners.
Cain Brothers developed a relationship with the founder, Robb Kolb, and discussed potential transaction alternatives. Collectively, the team decided to run a targeted process due to preemptive interest, with the option to expand into a broad sale if needed.
Premier Radiology is a leading provider of teleradiology solutions in outpatient settings across the United States, delivering fast, accurate, and secure medical image interpretations. Founded in 2006 and headquartered in Deerfield Beach, Florida, the company interprets over three million medical images annually through a network of more than 165 board-certified, fellowship-trained radiologists.
Grovecourt is a private equity firm based in West Palm Beach, Florida, specializing in investments in founder-led and family-owned businesses in the lower middle market business services and healthcare services sectors.

acquired by

Sell-Side Advisor
Summary
On January 27, 2026, Makarora Management LP (Makarora) announced that, together with Ares Alternative Credit funds (Ares), it completed the previously announced all-cash acquisition of Plymouth Industrial REIT, Inc. (Plymouth), valued at approximately $2.1 billion. Pursuant to the terms of the transaction, Plymouth shareholders will receive cash consideration of $22.00 per share. With the completion of the acquisition, Plymouth will no longer be traded or listed on any public securities exchange.
KeyBanc Capital Markets served as a Sell-Side Advisor to Plymouth Industrial REIT.
Plymouth Industrial REIT, Inc. (NYSE: PLYM) is a full-service, vertically integrated real estate investment company focused on the acquisition, ownership and management of single and multi-tenant industrial properties.
Makarora Management LP is a New York-based investment management firm established in 2024 and led by senior professionals with extensive experience investing through global property market cycles. The firm seeks to provide differentiated capital solutions to the commercial real estate sector spanning a wide range of investments, including opportunistic credit, structured capital, and equity.
Ares Management Corporation (NYSE: ARES) is a leading global alternative investment manager offering clients complementary primary and secondary investment solutions across the credit, real estate, private equity and infrastructure asset classes. As of September 30, 2025, Ares Management Corporation's global platform had over $595 billion of assets under management, with operations across North America, South America, Europe, Asia Pacific and the Middle East.

$859.3 Million
Initial Public Offering
Joint Bookrunner
Summary
On January 22, 2026, KeyBanc Capital Markets served as Joint Bookrunner on EquipmentShare.com Inc.’s (EquipmentShare or the Company) $859.3 million Initial Public Offering of 35,075,000 shares, including overallotment.
EquipmentShare is a digitally native equipment rental platform serving primarily non-residential construction end markets. Enabled by its technology platform, T3, which provides real-time telematics, management, and predictive maintenance of its fleet, the Company offers a tech-forward, seamless equipment rental experience. EquipmentShare serves customers with an integrated solution designed to make their jobsites more efficient, safer, and lower cost.

$500 Million
Senior Notes
Co-Manager
Summary
On January 8, 2026, KeyBanc Capital Markets served as Co-Manager on a $500 million Senior Notes offering for Murphy Oil Corporation. Proceeds will be used to repay existing indebtedness and for general corporate purposes.

$1.05 Billion
Senior Secured Credit Facilities
Summary
On November 3, 2025, KeyBanc Capital Markets Inc. (KBCM) successfully closed $1.05 billion of Senior Secured Credit Facilities (the Facilities) for Apex Clean Energy (Apex). The Facilities are comprised of a $500 million Term Loan Facility, a $400 million Letter of Credit Facility, and a $150 million Revolving Credit Facility. Proceeds will be used to fund Apex’s next phase of growth. KBCM acted as Coordinating Lead Arranger.
Apex Clean Energy Overview
Apex Clean Energy was founded with a singular focus: to accelerate the shift to clean energy. Through origination, development, construction, and operation of utility-scale wind, solar, and storage facilities and distributed energy resources, Apex is expanding the renewable frontier across the United States. The company’s mission-driven team uses a data-focused approach and an unrivaled portfolio of projects to create solutions for the world’s most innovative and forward-thinking customers.

Twisp Family Haven
$10.9 Million
Construction Loan
Summary
KeyBank Community Development Lending & Investment provided capital for the new construction of Twisp Family Haven, a 48-unit affordable housing project in Twisp, Washington. 48 units will serve families and individuals earning no more than 30–60% Area Median Income (AMI). 20 units will be set aside for Permanent Supportive Housing (PSH), with 8 units receiving project-based Section 8 vouchers and 12 units reserved for households who are or have experienced homelessness. Supportive services will be offered to all residents by Room One and will include case management, transportation, assistance in accessing employment, and drug and alcohol counseling. We want to thank Catholic Charities of Eastern Washington for their sponsorship and shared mission to build much-needed affordable housing in Washington.
The financing includes a $10.9 million construction loan arranged by Caleb Stephens.

acquired

Buy-Side Advisor
Summary
Cain Brothers, a division of KeyBanc Capital Markets, served as exclusive financial advisor to Tenor Health Foundation in its acquisition of Commonwealth Health, an affiliate of Community Health Systems, Inc. (NYSE: CYH). Cain Brothers also arranged debt financing associated with the transaction.
Tenor Health acquired Commonwealth Health, a subsidiary of Community Health Systems. Commonwealth is a three-hospital health system in northeast Pennsylvania that includes Regional Hospital of Scranton (186 beds), Moses Taylor Hospital (122 beds) and Wilkes-Barre General Hospital (369 beds). Rosemawr Management provided acquisition financing.
With a mission rooted in advancing equitable and innovative care, Tenor Health Foundation was formed to identify, own, manage, and turn around financially challenged hospitals. Tenor Health is committed to the needs of its communities, providing compassionate care and delivering quality patient outcomes.
Community Health Systems operates 70 affiliated hospitals in 14 states, as well as more than 1,000 sites of care, including physician practices, urgent care, freestanding emergency and occupational medicine clinics, and imaging, cancer and ambulatory surgery centers. CHS reported consolidated annual revenues of over $12 billion.

affiliated with

Sell-Side Advisor
Summary
Cain Brothers, a division of KeyBanc Capital Markets, served as financial advisor to FHN in its affiliation with Mercyhealth.
After years of discussion, FHN elected to pursue a change-of-control transaction with the goals of improving the organization’s cost structure and injecting outside capital. Cain Brothers led a competitive process, resulting in two fully negotiated letters of intent. The Board selected Mercyhealth, out of Rockford, Illinois, who committed to contribute a minimum of $100 million over five years. The transaction was signed on September 30, 2025, and closed on December 31, 2025.
FHN is a regional healthcare system serving northwest Illinois and southwest Wisconsin. FHN is headquartered in Freeport, Illinois and consists of a 100-bed full-service hospital known as FHN Memorial Hospital, 16 outpatient sites that treat over 45 specialties, a comprehensive Cardiovascular Center and a leading Cancer Center. Over 1,500 people visit FHN each day, and FHN is one of the leading employers in northwest Illinois.
Mercyhealth is an Illinois not-for-profit system serving northern Illinois and southern Wisconsin. Mercyhealth operates five acute-care hospitals with over 500 beds, a large multi-specialty physician group, over 85 primary and specialty care clinics, a rehabilitation hospital, and a significant home health and hospice business. Mercyhealth was created after the merger of Mercy Health in Janesville, Wisconsin and Rockford Health System in Rockford, Illinois. Mercyhealth produced $1.3 billion in revenue in 2025.

Cedar Commons II
$15 Million
Construction Loan
Summary
KeyBank Community Development Lending & Investment provided capital for the new construction of Cedar Commons II, a 64-unit senior affordable housing project in Bellingham, Washington. All 64 units will serve senior citizens earning no more than 30%-60% Area Median Income (AMI). The property will feature 26 Permanent Supportive Housing (PSH) units, with 13 units reserved for households with one or more physically disabled member and 13 units reserved for senior citizens who are or have experienced homelessness. We want to thank Opportunity Council and Shelter Resources for their sponsorship and shared mission to build much-needed affordable housing in Washington.
The financing includes a $15 million construction loan arranged by Caleb Stephens.

Casa Del Pueblo Senior Apartments
$10.1 Million
Construction Loan
Summary
KeyBank Community Development Lending & Investment (CDLI) provided a $10.1 million construction loan on behalf of Chicanos Por La Causa (CPLC) to finance the acquisition and rehabilitation of Casa del Pueblo, a 9% LIHTC, 96-unit fully subsidized senior affordable housing property in Tucson, Arizona.
All the units are one bedroom and restricted to 40% area median income (AMI). The units are 100% occupied and the current tenants will not be displaced. Casa del Pueblo was originally constructed in two phases: one building in 1997 with 58 units and the other in 2011 with 38. The buildings feature three community rooms, fitness equipment, a computer room, lawn space with picnic area and a ramada with a barbecue. Services from the CPLC Healthy Aging program, such as congregate meals and health resources, are available for Casa del Pueblo residents to foster social, emotional, mental, and physical well-being.
CPLC is a nonprofit community development corporation with a 56-year history of empowering lives through more than 30 different programs across Arizona, California, Colorado, Nevada, New Mexico, and Texas, including efforts in affordable housing and community development, with over 3,000 units under management. KeyBank CDLI closed a different construction loan for CPLC in early 2025.
Matthew Haas from KeyBank CDLI structured the construction financing. Permanent financing was provided by the City of Tucson through HOME Investment Partnership Program (HOME) Funds, the State of Arizona through the Arizona Housing Trust Fund, and Rocky Mountain Community Reinvestment Corporation (RMCRC). The National Equity Fund (NEF) provided LIHTC equity.

Hub 27
$32.3 Million
Construction Loan, LIHTC Equity, and Bond Underwriting
Summary
KeyBank Community Development Lending & Investment provided capital for the new construction of Hub 27, a 53-unit affordable housing project in Cleveland, Ohio. All 53 units will serve families and individuals earning no more than 60%-70% Area Median Income (AMI). The property will feature amenities for residents, including bike storage, a clubhouse, courtyard with playground, fitness center, and a rooftop terrace and deck. We want to thank Pivotal Housing Partners and Metro West Development Organization for their sponsorship and shared mission to build much-needed affordable housing in Ohio.
The financing includes a $13.7 million construction loan arranged by David Lacki, $18.6 million in LIHTC equity arranged by Derek Reed, and bond underwriting provided by KeyBanc Capital Markets led by Sam Adams.

Benning Road Metro Apartments
$55.3 Million
Construction Loan and Permanent Loan
Summary
KeyBank Community Development Lending & Investment provided capital for the new construction of Benning Road Metro Apartments, a 109-unit affordable housing project in Washington, D.C. All 109 units will serve families and individuals earning no more than 30%-80% of Area Median Income (AMI). The property will feature 22 units of Permanent Supportive Housing (PSH) to be covered by vouchers administered by the Local Rent Supplement Program (LRSP). Supportive services will be offered to residents, facilitated by the project’s development partner, Marshall Heights Community Development Organization, and will include workshops about financial management, employment readiness, entrepreneurship, and rental counseling. We want to thank The NRP Group for their sponsorship and shared mission to build much-needed affordable housing in Washington, D.C.
The financing includes a $43.7 million construction loan arranged by Seaver Rickert and a $11.6 million permanent loan arranged by Robbie Lynn.

Atkinson Stacks & Sunrise Metro
$43.4 Million
Construction Loan and Permanent Loan
Summary
KeyBank Community Development Lending and Investment (CDLI) provided a $27.3 million construction loan on behalf of the Housing Authority of Salt Lake City (HASLC) to finance the rehabilitation and new construction of Permanent Supportive Housing and a subsidized apartment community in Salt Lake City. KeyBank’s Commercial Mortgage Group (CMG) also arranged permanent financing with a $16 million Freddie Mac 9% LIHTC forward commitment. The rehabilitation and new construction will consist of 218 units:
- Sunrise Metro – Renovation of existing 100-unit, four-story structure with the addition of 18 new units to the second floor
- Atkinson Stacks – New construction of 100-unit, six-story structure
Units are restricted at 25%-35% of area median income (AMI) across six studios and 212 one-bedrooms. The new building will include commercial space on the bottom floor to be occupied by Sacred Circle, a supportive services and case management provider. Sacred Circle will provide substance abuse counseling, employment, financial support and other services as needed. They will also operate a clinic and pharmacy.
Unit amenities include kitchen range, refrigerator, laminate countertops, and vinyl floors. Property amenities currently in Sunrise Metro include a courtyard, garden, dog run, case management offices, supportive service spaces, and a food pantry. With the expansion and renovation, the HASLC is adding a gym, programmed outdoor spaces, a pharmacy, and a medical clinic to be staffed by Sacred Circle Healthcare, projected to have 12 full-time employees at the site.
“We sincerely thank KeyBank for supporting this transformative project,” Daniel Nackerman, Executive Director, Housing Authority of Salt Lake City noted. “The new and renovated housing will offer safe, affordable homes along with essential services that uplift residents. By promoting community and stability, we are making notable progress toward improving lives and strengthening neighborhoods in Salt Lake City.”
The federal and state LIHTC credits will be purchased/syndicated by The Richman Group. Rachel Grudzien of KeyBank CDLI and Hector Zuñiga of KeyBank CMG structured the financing.

acquired
and was recapitalized by

and

$1.07 Billion
Senior Secured Credit Facilities
Joint Lead Arranger
Joint Bookrunner
Administrative Agent
Summary
KeyBanc Capital Markets and Cain Brothers successfully closed the syndication of $1.07 billion Senior Secured Credit Facilities for US Fertility Enterprises, LLC, a portfolio company of Amulet Capital Partners and L Catterton Partners.
Proceeds from the transaction supported the recapitalization of US Fertility, which included a new equity investment led by L Catterton and the Company’s acquisition of Genetics & IVF Institute. The financing was comprised of a $120 million Revolving Credit Facility, an $825 million Term Loan B, and a $125 million Delayed Draw Term Loan.
KBCM was selected to serve as Joint Lead Arranger and Administrative Agent based on Cain Brothers’ expertise in the women’s health space, our long-standing relationship with Amulet Capital Partners, and our best-in-class leveraged finance platform.
US Fertility is the largest fertility group in the U.S., offering a broad range of assistive reproductive technology services and ancillary life sciences offerings. Since 2021, the Company has grown from ~85 physicians across 59 locations to the leading IVF platform in the nation with over 200 physicians across 118 treatment locations and 32 embryology labs.
Founded in 2015, Amulet Capital Partners is a middle-market private equity firm focused exclusively on making investments in the broader healthcare industry. They have $2.7 billion in AUM and are currently investing out of their third fund. Amulet partners with strong businesses across high-conviction, high-growth subsectors within the broader life sciences outsourcing, healthcare provider, and payor and payor services ecosystems.
Founded in 1989, L Catterton is the largest consumer-focused private equity firm in the world, with over $38 billion of equity capital across nine fund strategies in 18 offices globally. They have $38 billion in AUM and have extensive experience in consumer healthcare and multi-site service platforms. L Catterton has an operationally focused value creation approach, augmented by a deep operating team with highly differentiated capabilities.

West Branch & River Road Apartments
$16.7 Million
Equity Bridge Loan and Permanent Loan
Summary
KeyBank Community Development Lending & Investment provided capital for the acquisition and rehabilitation of West Branch & River Road Apartments, a two-property affordable housing portfolio totaling 68 units in Stowe, Vermont. The portfolio will benefit under a project-based Section 8 contract serving families, seniors, and disabled individuals earning no more than 50%-60% of Area Median Income (AMI). The property will feature amenities for residents including onsite laundry and a community clubhouse. We want to thank Steele Properties for their sponsorship and shared mission to preserve much-needed affordable housing in Vermont.
The financing includes a $4.5 million equity bridge loan arranged by Rachel Grudzien and a $12.2 million construction-to-permanent loan arranged by Hector Zuniga.

Waterville Senior Lofts
$13.8 Million
Construction Loan
Summary
KeyBank Community Development Lending & Investment provided capital for the new construction of Waterville Senior Lofts, a 70-unit senior affordable housing project in Toledo, Ohio. All 70 units will serve senior citizens who earn no more than 30%-70% of Area Median Income (AMI). Supportive services will be provided by St. Mary Development Corporation and will include transportation, meals on wheels, housekeeping, and workshops on topics such as financial literacy, nutrition, fitness, and the arts. We want to thank Pivotal Housing Partners and Neighborhood Housing Services of Toledo, Inc for their sponsorship and shared mission to build much-needed affordable housing in Ohio.
The financing includes a $13.8 million construction loan arranged by David Lacki.

acquired

Buy-Side Advisor
Summary
Cain Brothers, a division of KeyBanc Capital Markets, acted as buy-side advisor to Gauge Capital on its acquisition of Reliable Medical from Seven Hills Capital.
Cain Brothers maintains an ongoing dialogue with Gauge on M&A opportunities and was engaged based on our expertise in the Complex Rehabilitation Technology sector. Cain provided tactical and strategic process-related recommendations and insight, while advising Gauge on valuation and key diligence topics. The mandate further bolsters our credentials in the broader DME sector and as a trusted advisor to private equity firms.
Reliable Medical is a provider of CRT and related mobility and home medical equipment solutions across the U.S. Reliable specializes in the evaluation, fitting, assembly, and service of custom mobility solutions for patients with severe and permanent mobility impairments. The Company has built a strong reputation as a trusted clinical and service partner to patients, referral sources, and payors through its experienced Assistive Technology Professionals and high-touch service model. Reliable was founded in 1989 and is headquartered in Nashville, Tennessee.
Gauge Capital is a middle-market private equity firm based in Southlake, Texas. Gauge invests in five key sectors: business services, food & consumer, government & industrial services, healthcare, and technology. The firm manages more than $3 billion in capital.
Rose Creek Apartments
$36 Million
Construction Loan and Permanent Loan
Summary
KeyBank Community Development Lending & Investment provided capital for the new construction of Rose Creek Apartments, a 125-unit affordable housing project in Edmond, Oklahoma. All 125 units will serve families and individuals earning no more than 60% Area Median Income (AMI). The property will feature amenities for residents including a business center, courtyard, dog park, and a fitness center. We want to thank Express Development, Inc. for their sponsorship and shared mission to build much-needed affordable housing in Oklahoma.
The financing includes a $24.4 million construction loan arranged by Ted Witt and a $11.6 million permanent loan arranged by Hector Zuniga.

Riverplace Apartment Homes
$29.2 Million
Fannie Mae (Fixed-Rate Loan)
Summary
The transaction includes a $29.2 million ($143,098/unit) non-recourse, first mortgage loan secured by a 204-unit apartment complex known as Riverplace Apartment Homes, located in Independence, Oregon. Built in 2015, Riverplace Apartment Homes consists of three-story residential buildings, eight garage buildings, one clubhouse and one car wash situated on 10.13 acres of land. The proposed loan will be used for refinancing the existing debt of the property. The loan is structured with a 35-year term, and subsequent to a five-year interest-only period, amortizes on a 30-year schedule.

has sold a portfolio of operating DG solar and storage assets to

Exclusive Financial Advisor
Summary
KeyBanc Capital Markets, Inc. served as exclusive financial advisor to Greenbacker Renewable Energy Corporation (Greenbacker) on the sale of a diversified operating portfolio of distributed generation (DG) solar and storage assets (the Portfolio) to Altus Power, Inc. Representing one of the largest operating DG portfolios marketed in recent years, the Portfolio includes 237 MW across 101 ground mount, rooftop, and carport sites located in 18 states.
Greenbacker Overview
Greenbacker Renewable Energy Company LLC is a publicly reporting, non-traded limited liability sustainable infrastructure company that acquires and manages income-producing renewable energy and other energy-related businesses, including solar and wind farms. The company also provides investment management services to other renewable energy investment vehicles. Greenbacker seeks to acquire and operate high-quality projects that sell clean power under long-term contracts to creditworthy counterparties such as utilities, municipalities, and corporations. As a long-term owner-operator, Greenbacker strives to be a good steward of the land and a responsible member of the communities in which it operates.
Greenbacker conducts its investment management business through its wholly owned subsidiary, Greenbacker Capital Management, LLC, an SEC-registered investment adviser. The company believes its focus on power production and asset management creates value that can be passed on to shareholders — while facilitating the transition toward a clean energy future.
Altus Power Overview
Altus Power is a leading Independent Power Producer focused on the ownership, operation, and optimization of distributed solar generation assets across the United States. The company operates over one gigawatt of distributed generation assets, including rooftop, ground-mounted, and carport solar systems that serve commercial, industrial, municipal, and community solar customers. Backed by TPG, a global investment firm, Altus Power benefits from significant institutional support and access to capital. The company’s vertically integrated platform, experienced management team, and focus on high-quality distributed generation assets position it as a scaled consolidator and long-term owner within the U.S. solar market.

a portfolio company of



$1.564 Billion
Senior Secured Credit Facilities
$1.275 Billion
Senior Secured Notes
Joint Lead Arranger
Joint Bookrunner
Summary
KeyBanc Capital Markets and Cain Brothers, a division of KeyBanc Capital Markets, Inc., successfully closed a financing in support of Sevita, a portfolio company of Centerbridge Partners, Madison Dearborn Partners, and The Vistria Group.
Proceeds from the financing were used to acquire BrightSpring Health’s Community Living division and to refinance existing indebtedness. The transaction consisted of a $314 million Revolving Credit Facility, a $875 million Term Loan B, a $375 million Delayed Draw Term Loan B, and $1.275 billion of Senior Secured Notes.
Sevita is a national provider of home and community-based services to specialized, complex patient populations with a range of medical, behavioral, and social needs. Since being founded in 1980, the Company has evolved from a single residential program to a diversified network operating across 40 states with 43,900+ individuals served.
Centerbridge Partners is a New York City-headquartered private investment firm with $18 billion of capital commitments and $38 billion of AUM. Founded in 2005, Centerbridge seeks to back strong management teams to drive operational improvements and other value creation strategies.
Founded in 1992, Madison Dearborn Partners is a Chicago-based private equity firm, with $19 billion of committed capital, focusing on the Basic Industries, Financial Services, Healthcare, and Technology & Government sectors.
Headquartered in Chicago and founded in 2013, The Vistria Group is a private equity firm focused on investing in the Education, Financial Services, and Healthcare sectors with $7 billion of AUM across 40+ portfolio companies.

Atkinson Stacks Sunrise Metro
$16 Million
Freddie Mac (Fixed-Rate Loan)
Summary
The transaction includes a $16 million ($73,578/unit) non-recourse, first mortgage loan secured by a proposed 218-unit, affordable, multifamily apartment community known as Atkinson Stacks Sunrise Metro, located in Salt Lake City, Utah. The property consists of an existing 100-unit, four-story structure called Sunrise Metro, with an addition of 18 new units to the second floor (hereinafter referred to as “Phase I”) and new construction of Atkinson Stacks (proposed 100-unit, six-story structure, hereinafter referred to as “Phase II”). The structures are to be connected by an existing one-story common space. The construction/renovation of Phase I has commenced and has an estimated substantial completion of January 2026. The construction of Phase II is scheduled to commence December 2025, with an estimated duration of approximately 18 months for substantial completion in June 2027. The property is situated on a 2.7-acre site. The proposed loan will be used for substantial rehabilitation of the property. The loan is structured with a 16-year term, and subsequent to a one-year interest-only period, amortizes on a 40-year schedule.
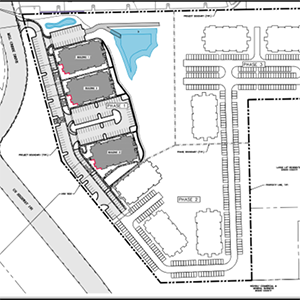
The Cooperative 1581
$17.98 Million
Freddie Mac (Fixed-Rate Loan)
Summary
The transaction includes a $17.98 million ($124,861/unit) non-recourse, first mortgage loan secured by a to-be-built, 144-unit, Low-Income Housing Tax Credit (LIHTC), garden-style apartment complex known as The Cooperative 1581, located in Moab, Utah. The project will consist of three three-story walk-up buildings and will be 100% income- and rent-restricted, targeting households earning between 40% and 80% of the Area Median Income (AMI), with a blended average of 60% AMI. Expected construction completion is scheduled for April 2027. The Subject will be situated on a 5.64-acre site. The proposed loan will be used for construction of the property. The loan is structured with a 15-year term and amortizes on a 40-year schedule.

a portfolio company of

$350 Million
Senior Secured Credit Facilities
Summary
KeyBanc Capital Markets and Cain Brothers, together with the KeyBank Beach Point Direct Lending Program, successfully closed on $350 million of Senior Secured Credit Facilities for Wedgewood Pharmacy, a portfolio company of Partners Group.
The Credit Facilities supported a refinancing of the Company’s existing debt and consisted of a $40 million Revolving Credit Facility and a $310 million Unitranche Term Loan.
Wedgewood, based in Swedesboro, New Jersey, is the nation’s leading compounding pharmacy dedicated to animal health. Since 1991, it has served veterinarians and animals of all species by providing high-quality, customized medications. The Company operates six compounding and outsourcing facilities across the U.S., along with an analytical testing laboratory, ensuring safe and efficient production of tailored medicines.
Partners Group is one of the largest firms in the global private markets industry, with around 2,000 professionals and over $174 billion in assets under management globally. The firm has investment programs and custom mandates spanning private equity, private credit, infrastructure, real estate, and royalties. The firm is based in Switzerland with a primary presence in the Americas in Colorado.

$300 Million
Debentures December 2025
$500 Million
Debentures September 2025
Active Joint Bookrunner
Summary
In December 2025, Wisconsin Electric Power successfully priced $300 million of Debentures maturing in 2029 at a spread of T+42 basis points, with a coupon of 3.950%. The transaction was well received by the market, achieving a minimal new issue concession and an orderbook oversubscription of 5.7 times, significantly exceeding the year-to-date average of 3.9 times. The differential between initial price guidance and final pricing was 28 basis points, which is also above the year-to-date average.
Similarly, in September 2025, the company priced $500 million of Debentures due 2030 at a spread of T+50 basis points for a coupon of 4.150%. This issuance also garnered strong market interest, pricing without a new issue concession and attracting an orderbook oversubscription of 4.9 times. The differential from initial price talk to final pricing reached 30 basis points, surpassing year-to-date averages.
KeyBanc Capital Markets served as Active Joint Bookrunner on both transactions. Proceeds from these offerings are intended to be used to repay existing short-term debt and for general corporate purposes.
About Wisconsin Electric Power Company
Wisconsin Electric Power Company (WEPCO) is a public utility that generates and distributes electricity and distributes and transports natural gas to retail customers in southeastern Wisconsin, including the Milwaukee area, east central Wisconsin, and northern Wisconsin. WEPCO provides wholesale electric service to various customers, including electric cooperatives, municipal joint action agencies, investor-owned utilities, etc. The company serves roughly 1.2 million electric customers and 0.5 million natural gas customers. WEPCO operates as a subsidiary of WEC Energy Group.
Our Expertise
Explore the latest information and expertise from our team of industry specialists covering solutions for capital growth, business expansion, and financial strategies.
Banking products and services are offered by KeyBank National Association. All credit products are subject to collateral and/or credit approval, terms, conditions, and availability and subject to change.
Key Wealth, Key Private Bank, Key Family Wealth, KeyBank Institutional Advisors and Key Private Client are marketing names for KeyBank National Association (KeyBank) and certain affiliates, such as Key Investment Services LLC (KIS) and KeyCorp Insurance Agency USA Inc. (KIA).